Cybersecurity in IT contracting
Published on 3rd May 2021
Allocating risk with regard to liability for IT security in contractual negotiations requires a clear understanding of each party's responsibilities

In our previous Insight, we tackled the qualification of certain legal obligations as regards IT security and concluded that IT security as an obligation of result is difficult to maintain. In this Insight, we focus on certain liability aspects with regard to IT security.
In general, liability is one of the most controversial topics in a contract negotiation. This is certainly the case when the discussions about liability and the damages to be awarded revolve around the liability for IT security breaches. All too often companies aim to shift their liability and risk as much as possible to the other contracting party. In doing so, they may be maintaining the (sometimes unreasonable) expectation that the other party will assume the full liability risk for damages resulting from cybersecurity incidents.
However, such discussions are often futile as they fail to take into account that IT and IT security are often a shared responsibility between the parties. Consequently, in order to have a meaningful discussion about liability regarding IT security, it is important to understand the so-called demarcation point of responsibilities.
Demarcation of responsibility in IT contracts
The IT stack
Databases, applications and IT systems do not operate on their own, they form part of a larger environment which enables them to operate. Generally speaking, an IT system is represented as a stack of different components (see illustration below), each of which is necessary for the system to operate:
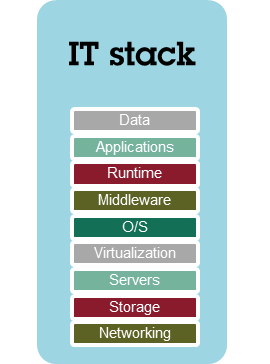
In terms of IT security, each of these layers could be subject to an IT security breach. So the IT security in the environment illustrated above is only as good as the weakest component in the stack.
Demarcation of risks – a reality check
As part of IT outsourcing projects, customers often request vendors to assume full end-to-end responsibility for their systems. Consequently, customers have a tendency to shift all responsibilities with regard to IT systems to the vendor concerned. This problem is typically encountered in standard procurement contracts that provide for boilerplate contract clauses which are often not suited for the IT project at hand. Although shifting the full liability to a vendor might be understandable, it is not always a suitable approach and is likely to create unnecessary friction at the negotiation table.
In Infrastructure as a Service (IaaS) projects for instance, a customer will only outsource a part of the IT stack to a vendor. In such contracts, the customer typically requests the vendor to host and manage the physical IT infrastructure (the lower layers of the stack) in a data centre whereas the higher layers of the stack are still managed by the customer itself or by a third party (see illustration below):

As part of an IaaS solution, a vendor will generally obtain the necessary LAN/WAN connectivity solution, acquire, manage and maintain storage systems and servers, and deploy and maintain a virtualisation system, and in some cases an operating system, on such systems. Conversely, the customer, or a third party appointed by the customer, will be responsible for maintaining the software layer, allocating appropriate permissions and handling the data itself.
In such a scenario, shifting the full liability risk to the IaaS vendor might be inappropriate. This is even more the case as liability law typically provides that a party is only responsible for its own actions or for those of the persons or objects under its responsibility.
If, in such a context, a cybersecurity incident occurred that would solely be attributable to the application layer for instance (which, in this example, would be managed by the client itself), one could hardly argue that such an incident would trigger the liability of the vendor.
When negotiating on responsibilities and the resulting liabilities in this setup, it would make more sense to abstain from the ambition to shift the entire liability risk to the vendor and instead to retain a more realistic and pragmatic allocation of risk.
Osborne Clarke comment
To avoid difficult and fruitless discussions on liability and IT security, it is imperative that the actors in those discussions understand the technology that is offered or sourced and understand its legal and operational consequences. Based on that analysis, the contracting parties can align with each other's expectations, tailor each other's roles and responsibilities accordingly, and allocate the liability risk through proper contract drafting.



